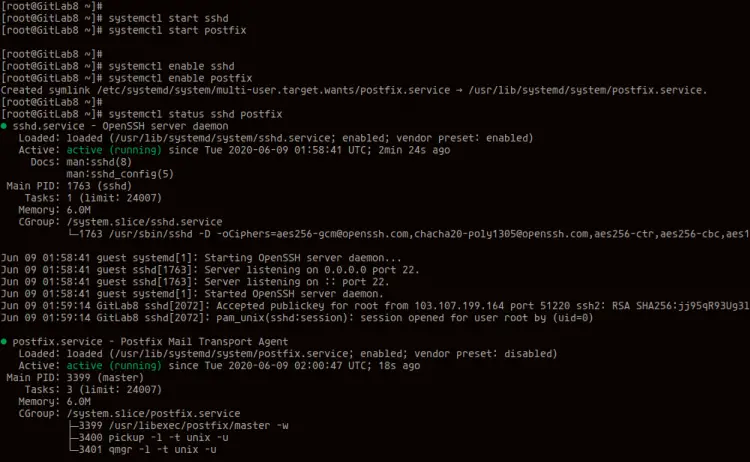
Shared runners are general purpose and can be used by multiple projects. The GitLab SaaS instance hosted on GitLab Inc has some shared runners that will automatically pick up your pipelines as explained in Step Three. Runners take jobs from your configurations based on an algorithm that accounts for the number of jobs currently being executed for each project. A shared runner is more flexible than a specific runner. It can be configured from the admin account of the GitLab instance.

Let's see how we can go about getting the tokens for both runners. We also managed to set up a GitLab CI runner on a separate host. We registered it to take jobs from our GitLab instances whenever there is a trigger. While this was a simple project, you can build on this information to set up pipelines for complex projects. The steps for adding a project to GitLab and linking a GitLab CI runner remain the same.

The things that change are the instructions and stages in the gitlab-ci.yml file. This can be found by running sudo gitlab-runner list on the machine with the runner installed. If you've already removed the runner in the gitlab runners page, it will still be present on the gitlab-runner machine (check with the command sudo gitlab-runner list ). Project-specific runners are applicable if you have unique requirements for the runner.
Another consideration is if your continuous integration stages have resource-intensive processes. Then, it would be ideal to go with a project-specific runner. Note that, a project-specific runner does not accept jobs from other projects.

You will configure the pipeline to build a Docker image, push it to the To achieve this, you'll store the SSH private key in a GitLab CI/CD variable . In order to install the gitlab-runner service, you'll add the official. In this tutorial, you learned how you can automate your tests with GitLab CI. We started by setting up a Node.js app project on GitLab. The project included some test cases and a gitlab-ci.yml. We learned that GitLab uses the gitlab-ci.yml file to determine what to do when it's triggered.

A gitlab-ci.yml file is just a configuration file that contains instructions on building and testing applications, written in YAML format that a GitLab CI runner can understand. Linux rpm post- how to install python3 on Linux server Using RPM How to install gitlab-runner to CentOS/fedora. To register the runner with GitLab first you need to get a registration token from the GitLab web interface. It is generated by GitLab and it can be found in your projects settings undersettings/ci_cd/Set up a specific Runner manually.
Click the Disable Shared runners button on the Runners Page so we can just use our runner register just now on each build. After commiting .gitlab-ci.yml (the file that is used by GitLab Runner to manage your project's build), we will see jobs running in the Builds Page on each push. We will start by creating a project repository on GitLab.
We are going to base this tutorial on a Node.js application. Since we do not want to create the project files from scratch, GitLab offers a tool to import projects from other version control repositories that we will make use of. The application we are importing is a simple "hello world" app built with Express.js – a minimalist web framework for Node.js applications.

We will be implementing the tests using Mocha and Chai – these are JavaScript frameworks used for unit testing. Mocha enables asynchronous testing, test coverage reports, and can be paired with other assertion libraries. It can be paired with any test framework, for our case, we will be pairing Mocha with Chai. NoteIfgitlab-runneris installed and run as service , it will run as root, but will execute jobs as user specified by theinstallcommand. If gitlab-runner is installed and run as service , it will run as root, but will execute jobs as user specified by the install command.

It is now time to make use of the second server we declared in the Prerequisites section of this tutorial. We will be installing and setting up a GitLab runner service on this server. You can deploy the service to run multiple runner instances for different projects on GitLab.
However, it's recommended to go with a descriptive name since they are used in the GitLab UI – this can be helpful during debugging. You will find most configurations on the web combining npm install with the commands in the test stage. We only separated them to help demonstrate how jobs interact since this is quite a small project.
The stage directive marks this job as build – it's run in the build stage. We will start by setting up a Git repository to host the code. Then, we will configure a CI process to monitor commits to the repository and initiate a CI runner to run the tests in an isolated Docker container. The fair usage queue algorithm assigns jobs based on the projects that have the fewest number of jobs already running on shared runners. GitLab is an emerging tool that empowers one of the pillars of DevOps called the CICD Pipeline.
Since GitLab is a very popular VCS tool, it is contained to implement CI on Commit to any branch or in the event of Merge Request. So, GitLab Runners can be configured to execute any sort of Project Repository CI Pipeline. In this article, we will discuss How to Configure GitLab CI runner on your own. It uses NGINX or Apache as a web front end to proxypass the Unicorn web server.

By default, communication between Unicorn and the front end is via a Unix domain socket but forwarding requests via TCP is also supported. The web front end accesses /home/git/gitlab/public bypassing the Unicorn server to serve static pages, uploads (e.g. avatar images or attachments), and precompiled assets. GitLab serves web pages and the GitLab API using the Unicorn web server. It uses Sidekiq as a job queue which, in turn, uses Redis as a non-persistent database backend for job information, meta data, and incoming jobs.
With GitLab installed, you can now configure SSL, the domain name or subdomain name passwords, and much more. The tutorial will go over the basic setup options that should be done. However, you can do alternative settings to those listed below. Here is where you will choose whether you want this runner to be project specific or shared. You can only provide one of the tokens you copied earlier for either of the options. Copy the registration token displayed on the right-hand side under Set up a shared Runner manually.

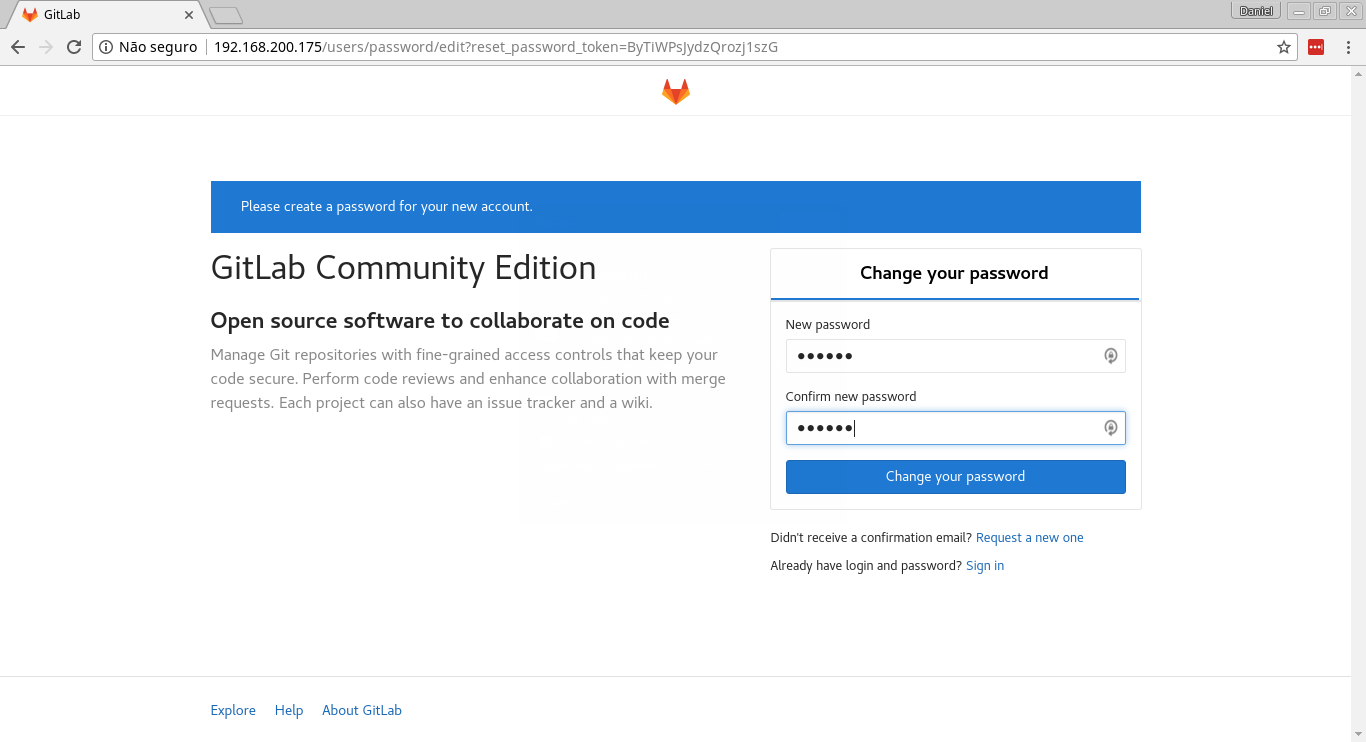
You will use the token to register the runner in the next step. You can choose to disable shared runners for this project by flipping the switch on the right-hand section under Shared Runners. Then, copy the registration token displayed to your notepad, as we will use it later. You will be happy to know that once your repository has the .gitlab-ci.yml file, any new commits you push to it will trigger a new Continuous Integration run.
For the case of self-managed GitLab instances, if you have not configured a GitLab runner, the CI run will be set to "pending". With your own runner you're no longer constrained by the limitations of the (totally awesome!) GitLab shared runners. You can run jobs with impunity, not giving a moment's thought to running into those resource limits. GPG public keys used for package metadata signature verification are installed automatically on first installation done with the instructions above. For key updates in the future, existing users need to manually download and install the new keys. The signature is verified when you use a command like apt-get update, so the information about available packages is updated before any package is downloaded and installed.
Verification failure should also cause the package manager to reject the metadata. This means that you cannot download and install any package from the repository until the problem that caused the signature mismatch is found and resolved. A native package called gitlab-ci-multi-runner is available in Debian Stretch. By default, when installing gitlab-runner, that package from the official repositories will have a higher priority. The add-on component GitLab Shell serves repositories over SSH.

It manages the SSH keys within /home/git/.ssh/authorized_keys which should not be manually edited. GitLab Shell accesses the bare repositories through Gitaly to serve Git objects and communicates with Redis to submit jobs to Sidekiq for GitLab to process. GitLab Shell queries the GitLab API to determine authorization and access. Once it's done we can use gitlab pages in our projects! Now you should be able to go to gitlab and see Pages section in project where pages deploy task was configured in .gitlab-ci.yml pipeline file... If you want to use dpkg / rpm instead of apt-get / yum, go through the first step to find the current GitLab version and then follow Update using a manually-downloaded package.
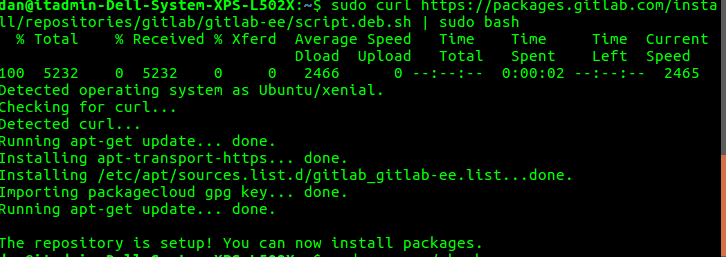
It's possible to upgrade to a newer version of GitLab without having to take your GitLab instance offline. If for some reason you don't use the official repositories, you can download the package and install it manually . To upgrade an existing GitLab Community Edition server installed using the Omnibus GitLab packages to GitLab Enterprise Edition , you install the EE package on top of CE. You have the option to deploy the runner on the same server that hosts your self-managed GitLab instance. However, to ensure an instance is not limited by resources, it's preferable to set up a separate CI runner instance.

Whichever configuration you choose to go with, Docker must be installed to isolate the test environments. The message indicates that the job is stuck because you have not configured any active runners that can execute this job. When you make a runner available, the job will start executing automatically. When a job executes, you will see the output on this interface as well as the other downloadable artifacts generated when the job was running.

The artifacts directive specifies files or directory paths to save and share between stages. Again, a reminder that ordering the stages properly is crucial to ensuring other files will have what they need to execute. The npm install command will install the dependencies in the node_modules directory. By declaring it in the artifacts, we make it available to jobs executed in subsequent stages. The files are also made available in the GitLab UI if you would like to download them. Defining caching helps minimize the time taken to run jobs that rely on resources that are unlikely to change between runs.

We specify the node_modules directory to be cached. This is the directory in which npm installs the dependencies for the project. To start, you will need a server running the GitLab version control software.

Both GitLab self-managed and SaaS can run automated tests. However, there are some limits in terms of minutes and resources made available to your tests in the free SaaS options. You have more freedom if you are using the self-managed options because you can allocate as many resources as you wish to your GitLab instance. Follow our tutorial on hosting your own Git Repositories with GitLab to learn how to set up your own GitLab instance.

The config.toml configuration file will be accessible at /srv/gitlab-runner/config/config.toml on the host machine. 🚨 If you do add a runner using the --docker-privileged then you'll probably want to be selective about what repositories have access to that runner. So, for example, it would probably be advisable to assign specific repositories to the runner rather than entire groups. Also, importantly, you'll want to disable any shared or group runners for those repositories so that they end up actually using this privileged runner.
I've got a project which takes a long time to build. However, the total time constraint has become a serious limitation . Then, run lxd init and configure the settings the way you want! Finally, run lxd-gitlab-runner.print-lxd-preseed | lxd init --preseed. The following steps describe launching a short-lived gitlab-runner container to register the container you created during install.

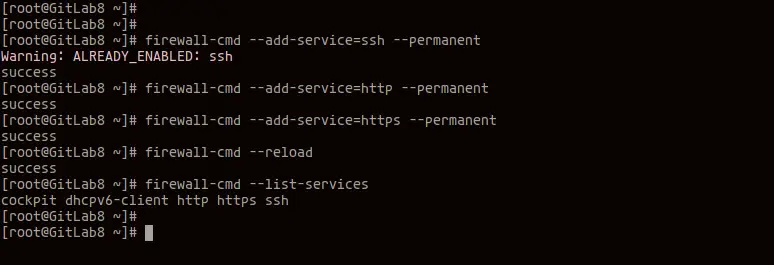
Git, which can be installed from the official site; A password for your user account, the problem by using Git to clean your directory structure, first run git config. GitLab Runner can use Docker to run jobs on user provided images. GitLab will support and release patches for the last 3 releases. In this step, we will download/install some packages needed for the GitLab installation.
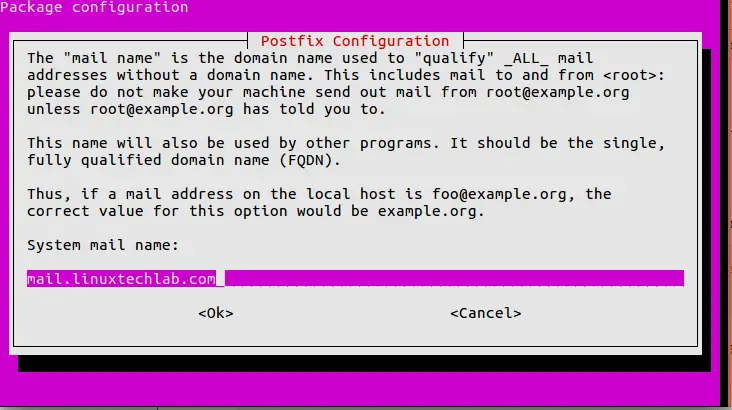
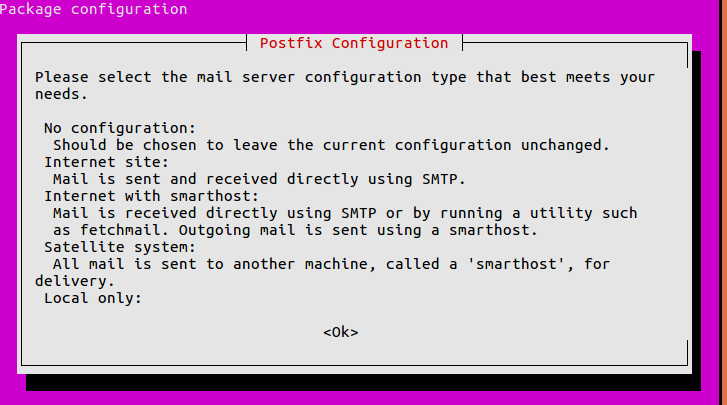
We will be using curl to download the repository installer, policycoreutils for SELinux manager, OpenSSH, and postfix as local SMTP server. Notice that when the build is triggered, it will use the registered docker+machine executor and creates a new instance in OpenStack. You can list the new instance on the OpenStack UI or by using the docker-machine ls command. You can find all the supported provider parameters listed in the GitLab repository. This example uses the OpenStack cloud platform for testing. We can configure the GitLab runner in terms of logging and cache settings, memory CPU settings, and more.

These settings can be done in the file called config.toml. This will be available after the installation of GitLab Runner. If you want to use our package, you should manually set the source of the package. The best way is to add the pinning configuration file. If you want to install GitLab from the source, then install some dependencies on the server and need to setup the database by using the PostgreSQL.

You can install the coordinator to build a web interface and control build instances. For more information, you can check the Installation of Coordinator chapter. The GitLab can be installed on Ubuntu system by using Omnibus package which provides different services to run GitLab. The Omnibus package provides necessary components of GitLab, establishes the configurations and project metadata which can be used in user's system.